Security in cloud computing is a major concern. Data in cloud should be stored in encrypted form. To restrict client from accessing the shared data directly, proxy and brokerage services should be employed.
Security Planning
Before deploying a particular resource to cloud, one should need to analyze several aspects of the resource such as:
- Select resource that needs to move to the cloud and analyze its sensitivity to risk.
- Consider cloud service models such as IaaS, PaaS, and SaaS. These models require customer to be responsible for security at different levels of service.
- Consider the cloud type to be used such as public, private, community or hybrid.
- Understand the cloud service provider’s system about data storage and its transfer into and out of the cloud.
The risk in cloud deployment mainly depends upon the service models and cloud types.
Understanding Security of Cloud
Security Boundaries
A particular service model defines the boundary between the responsibilities of service provider and customer. Cloud Security Alliance (CSA) stack model defines the boundaries between each service model and shows how different functional units relate to each other. The following diagram shows the CSA stack model:
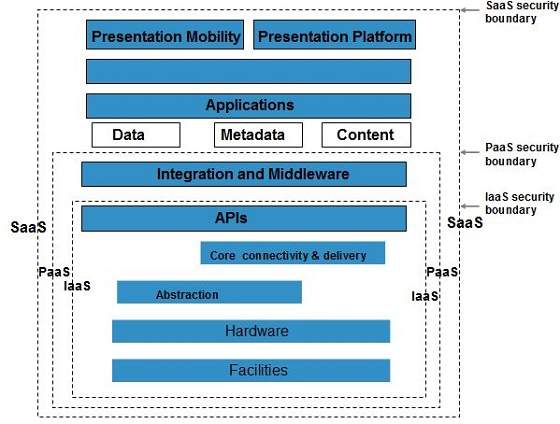
Key Points to CSA Model
- IaaS is the most basic level of service with PaaS and SaaS next two above levels of services.
- Moving upwards, each of the service inherits capabilities and security concerns of the model beneath.
- IaaS provides the infrastructure, PaaS provides platform development environment, and SaaS provides operating environment.
- IaaS has the least level of integrated functionalities and integrated security while SaaS has the most.
- This model describes the security boundaries at which cloud service provider’s responsibilities end and the customer’s responsibilities begin.
- Any security mechanism below the security boundary must be built into the system and should be maintained by the customer.
Although each service model has security mechanism, the security needs also depend upon where these services are located, in private, public, hybrid or community cloud.
Understanding Data Security
Since all the data is transferred using Internet, data security is of major concern in the cloud. Here are key mechanisms for protecting data.
- Access Control
- Auditing
- Authentication
- Authorization
All of the service models should incorporate security mechanism operating in all above-mentioned areas.
Isolated Access to Data
Since data stored in cloud can be accessed from anywhere, we must have a mechanism to isolate data and protect it from client’s direct access.
Brokered Cloud Storage Access is an approach for isolating storage in the cloud. In this approach, two services are created:
- A broker with full access to storage but no access to client.
- A proxy with no access to storage but access to both client and broker.
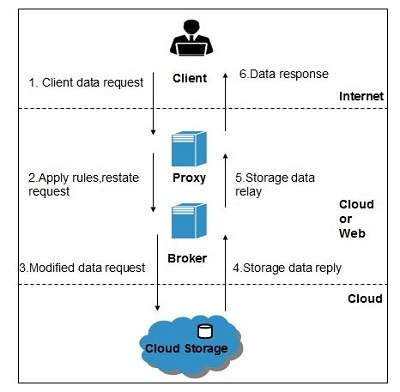
Working Of Brokered Cloud Storage Access System
When the client issues request to access data:
- The client data request goes to the external service interface of proxy.
- The proxy forwards the request to the broker.
- The broker requests the data from cloud storage system.
- The cloud storage system returns the data to the broker.
- The broker returns the data to proxy.
- Finally the proxy sends the data to the client.
All of the above steps are shown in the following diagram:
Encryption
Encryption helps to protect data from being compromised. It protects data that is being transferred as well as data stored in the cloud. Although encryption helps to protect data from any unauthorized access, it does not prevent data loss.
Cloud computing operation refers to delivering superior cloud service. Today, cloud computing operations have become very popular and widely employed by many of the organizations just because it allows to perform all business operations over the Internet.
These operations can be performed using a web application or mobile based applications. There are a number of operations performed in cloud. Some of them are shown in the following diagram:
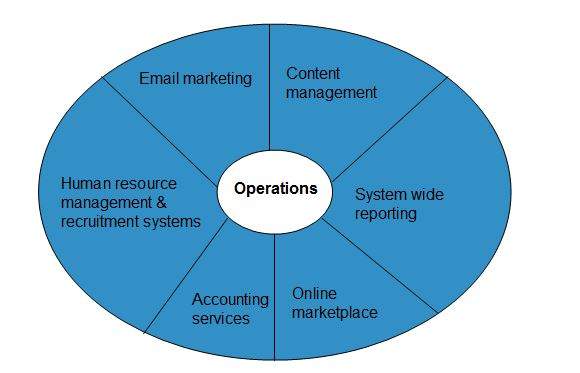
Managing Cloud Operations
There are several ways to manage day-to-day cloud operations, as shown in the following diagram:
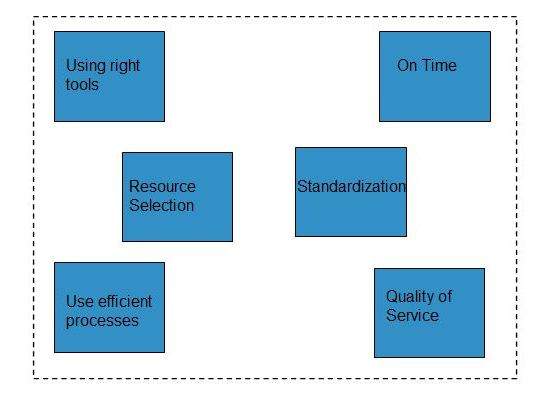
- Always employ right tools and resources to perform any function in the cloud.
- Things should be done at right time and at right cost.
- Selecting an appropriate resource is mandatory for operation management.
- The process should be standardized and automated to manage repetitive tasks.
- Using efficient process will eliminate the waste of efforts and redundancy.
- One should maintain the quality of service to avoid re-work later.
Cloud Computing has its applications in almost all the fields such as business, entertainment, data storage, social networking, management, entertainment, education, art and global positioning system, etc. Some of the widely famous cloud computing applications are discussed here in this tutorial:
Business Applications
Cloud computing has made businesses more collaborative and easy by incorporating various apps such as MailChimp, Chatter, Google Apps for business, and Quickbooks.
| SN | Application Description |
|---|---|
| 1 | MailChimp
It offers an e-mail publishing platform. It is widely employed by the businesses to design and send their e-mail campaigns. |
| 2 | Chatter
Chatter app helps the employee to share important information about organization in real time. One can get the instant feed regarding any issue. |
| 3 | Google Apps for Business
Google offers creating text documents, spreadsheets, presentations, etc., on Google Docs which allows the business users to share them in collaborating manner. |
| 4 | Quickbooks
It offers online accounting solutions for a business. It helps in monitoring cash flow, creating VAT returns and creating business reports. |
Data Storage and Backup
Box.com, Mozy, Joukuu are the applications offering data storage and backup services in cloud.
| SN | Application Description |
|---|---|
| 1 | Box.com
Box.com offers drag and drop service for files. The users need to drop the files into Box and access from anywhere. |
| 2 | Mozy
Mozy offers online backup service for files to prevent data loss. |
| 3 | Joukuu
Joukuu is a web-based interface. It allows to display a single list of contents for files stored in Google Docs, Box.net and Dropbox. |
Management Applications
There are apps available for management task such as time tracking, organizing notes. Applications performing such tasks are discussed below:
| SN | Application Description |
|---|---|
| 1 | Toggl
It helps in tracking time period assigned to a particular project. |
| 2 | Evernote
It organizes the sticky notes and even can read the text from images which helps the user to locate the notes easily. |
| 3 | Outright
It is an accounting app. It helps to track income, expenses, profits and losses in real time. |
Social Applications
There are several social networking services providing websites such as Facebook, Twitter, etc.
| SN | Application Description |
|---|---|
| 1 | Facebook
It offers social networking service. One can share photos, videos, files, status and much more. |
| 2 | Twitter
It helps to interact with the public directly. One can follow any celebrity, organization and any person, who is on twitter and can have latest updates regarding the same. |
Entertainment Applications
| SN | Application Description |
|---|---|
| 1 | Audio box.fm
It offers streaming service. The music files are stored online and can be played from cloud using the own media player of the service. |
Art Applications
| SN | Application Description |
|---|---|
| 1 | Moo
It offers art services such as designing and printing business cards, postcards and mini cards. |

0 Comments