Cloud Infrastructure as IDaaS and NaaS
Employees in a company require to login to system to perform various tasks. These systems may be based on local server or cloud based. Following are the problems that an employee might face:
- Remembering different username and password combinations for accessing multiple servers.
- If an employee leaves the company, it is required to ensure that each account of that user is disabled. This increases workload on IT staff.
To solve above problems, a new technique emerged which is known as Identity-as–a-Service (IDaaS). IDaaS offers management of identity information as a digital entity. This identity can be used during electronic transactions.
Identity
Identity refers to set of attributes associated with something to make it recognizable. All objects may have same attributes, but their identities cannot be the same. A unique identity is assigned through unique identification attribute. There are several identity services that are deployed to validate services such as validating web sites, transactions, transaction participants, client, etc. Identity-as-a-Service may include the following:
- Directory services
- Federated services
- Registration
- Authentication services
- Risk and event monitoring
- Single sign-on services
- Identity and profile management
Single Sign-On (SSO)
To solve the problem of using different username and password combinations for different servers, companies now employ Single Sign-On software, which allows the user to login only one time and manage the access to other systems. SSO has single authentication server, managing multiple accesses to other systems, as shown in the following diagram:
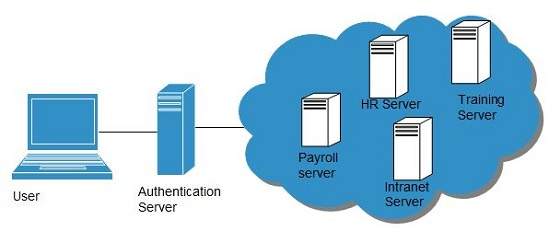
SSO Working
There are several implementations of SSO. Here, we discuss the common ones:
Following steps explain the working of Single Sign-On software:
- User logs into the
authentication server using a username and password.
The 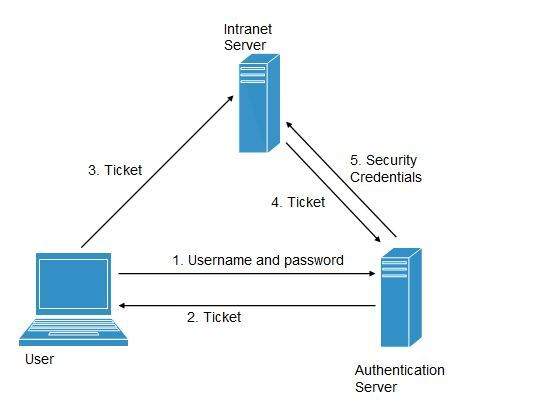 authentication server returns the user’s ticket.
authentication server returns the user’s ticket.
- User sends the ticket to intranet server.
- Intranet server sends the ticket to the authentication server.
- Authentication server sends the user’s security credentials for that server back to the intranet server.
If an employee leaves the company, then disabling the user account at the authentication server prohibits the user’s access to all the systems.
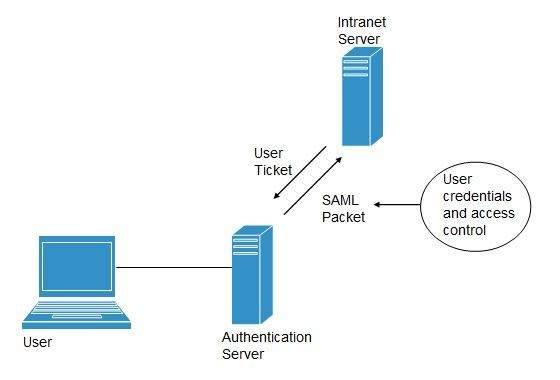
Federated Identity Management (FIDM)
FIDM describes the technologies and protocols that enable a user to package security credentials across security domains. It uses Security Markup Language (SAML) to package a user’s security credentials as shown in the following diagram:
OpenID
It offers users to login into multiple websites with single account. Google, Yahoo!, Flickr, MySpace, WordPress.com are some of the companies that support OpenID.
Benefits
- Increased site conversation rates
- Access to greater user profile content
- Fewer problems with lost passwords
- Ease of content integration into social networking sites.
Network-as-a-Service
Network-as-a-Service allows us to access to network infrastructure directly and securely. NaaS makes it possible to deploy custom routing protocols. NaaS uses virtualized network infrastructure to provide network services to the customer. It is the responsibility of NaaS provider to maintain and manage the network resources. Having a provider working for a customer decreases the workload of the customer. Moreover, NaaS offers network as a utility. NaaS is also based on pay-per-use model.
How NaaS is delivered?
To use NaaS model, the customer is required to logon to the web portal, where he can get online API. Here, the customer can customize the route. In turn, customer has to pay for the capacity used. It is also possible to turn off the capacity at any time.
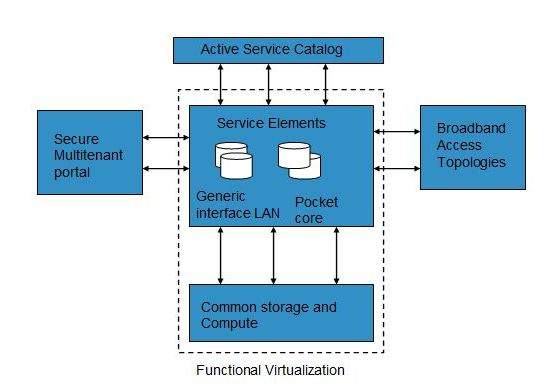
Mobile NaaS
Mobile NaaS offers more efficient and flexible control over mobile devices. It uses virtualization to simplify the architecture thereby creating more efficient processes. Following diagram shows the Mobile NaaS service elements:
NaaS Benefits
NaaS offers a number of benefits as discussed below:
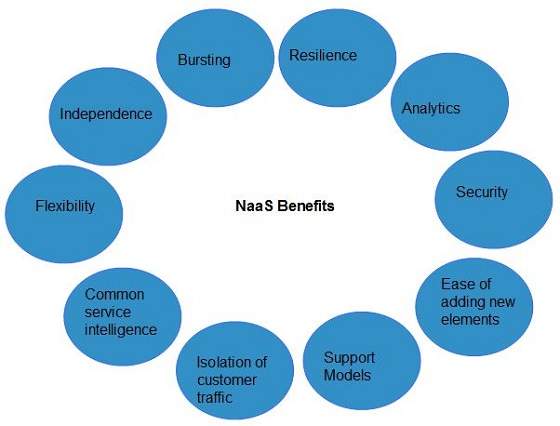
- Independence: Each customer is independent and can segregate the network.
- Bursting: The customer pays for high-capacity network only on requirement.
- Resilience: The reliability treatments are available, which can be applied for critical applications.
- Analytics: The data protection solutions are available, which can be applied for highly sensitive applications.
- Ease of Adding New Service Elements: It is very easy to integrate new service elements to the network.
- Support Models: A number of support models are available to reduce operation cost.
- Isolation of Customer Traffic: The customer traffic is logically isolated.

0 Comments